Access management: The secure approach to containing risk
Role-based access control, coupled with other unique technologies, means that Kinde is the only authorization provider that actually helps you prevent unauthorized access, reduce the risk of data breach when it does, and contain any damage done.
$4.2m The average cost of a data breach in 20211
Protect every part of your business
Make sure you safeguard your company, your team, your customers and your customer’s online presence.
The first line of defence
The most effective way to protect your data and eliminate threats is through a strong and robust access policy. Your team and customers can’t accidentally compromise data that they don’t have access to in the first place.
Roles before permissions
Controlling who can access which individual pieces of data and interface is critical to protecting your business and your customers. Hierarchical role-based access control (RBAC) allows for strict control and flexible assignment – aligning everything from your business view of the worldright down to the code you ship to customers.
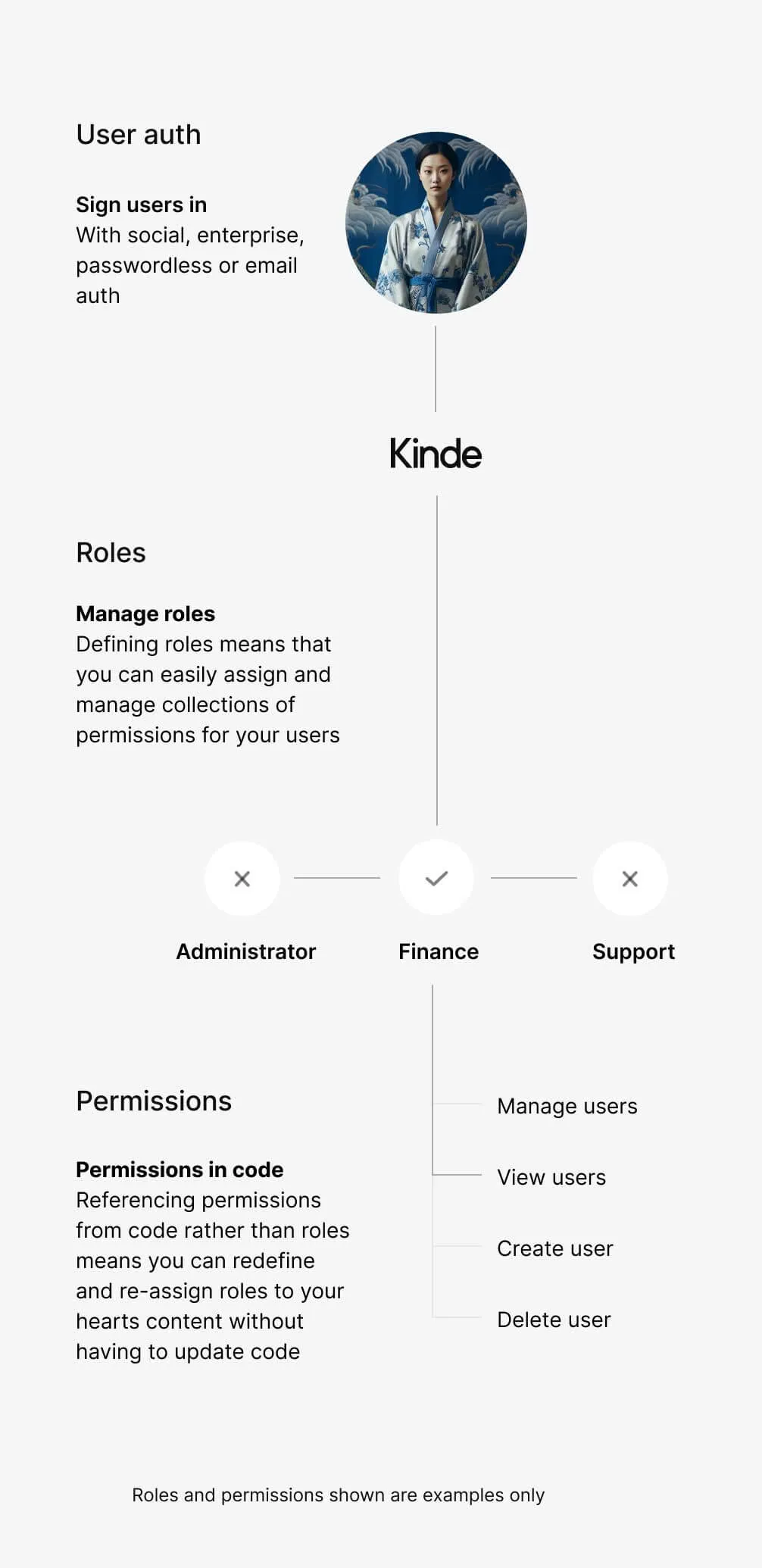
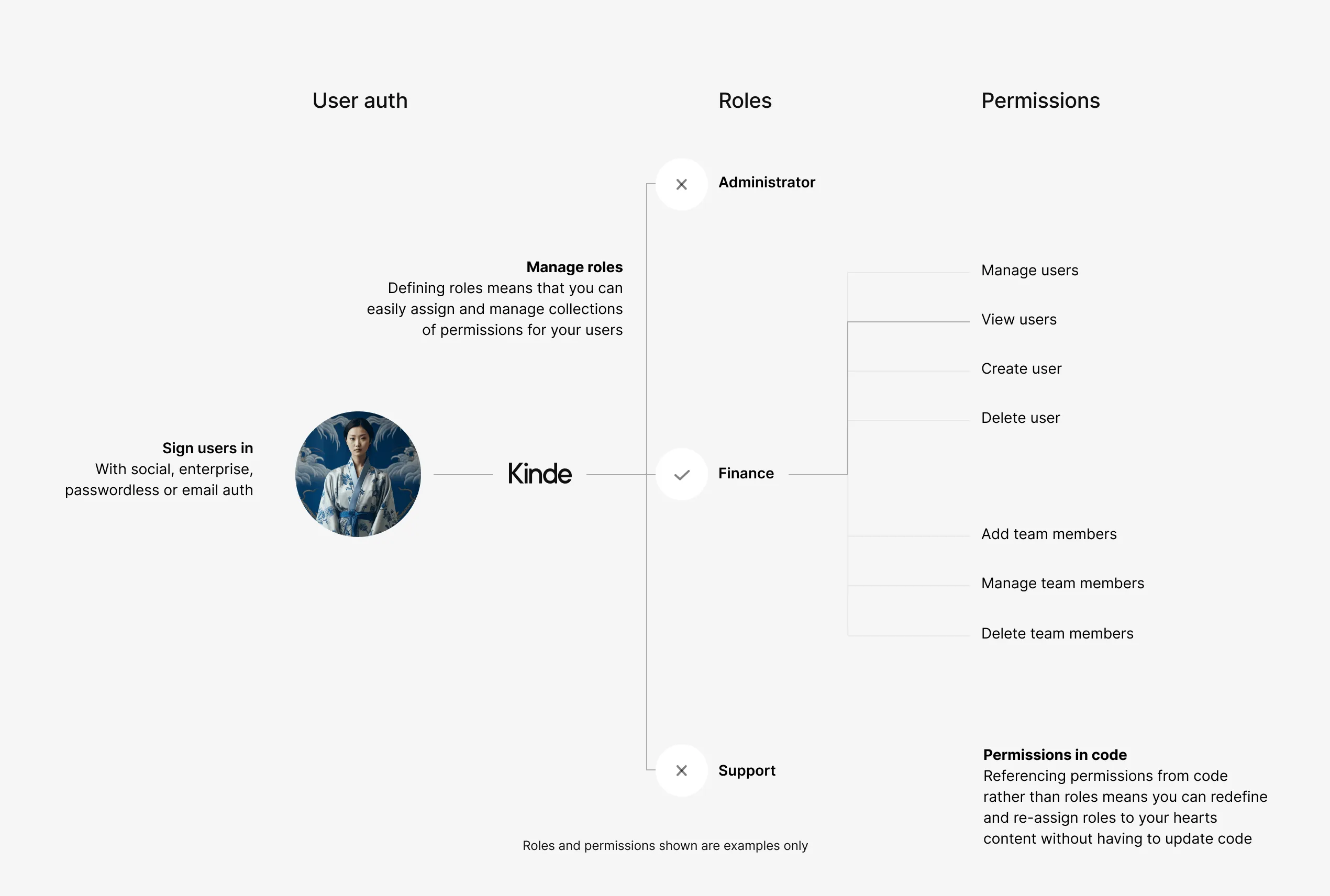
The triple threat against any threat
Layering on access control at every stage of the product cycle means layering on protection across the board without having to think about it. Kinde helps you build organizational best practice without any additional effort.
-
Environments
Separation of development and testing environments from production is essential in protecting your critical systems and user production data. Kinde environments enforce a strict layer of protection. Production data is safe. Your team doesn’t need to worry.
Learn more about Environments -
Organizations
Organizations provide an extra layer of protection and data isolation for any B2B business. User data is automatically siloed to its organization. Each organization has its own separate configuration which makes it easier to separate everything from branding to org credentials.
-
Feature flags
Empower your developers to deploy to production whenever they need to, without having to worry about things going public by mistake. This means your team decides when things go live and when data is accessible, even when code is in production.
Learn more about feature flags
Connected beyond
Connected apps allow your users to authenticate and maintain third-party machine-to-machine connections so that your product can share data and content seamlessly behind the scenes. Kinde connected apps manage access between your application and third parties so that you don’t have to. One less thing to worry about.
Learn more about connected apps
No compromise
The most effective way to control access is to prevent bad actors ever entering your systems. Kinde provides simple, powerful authentication with protection at every point of entry. Designed to maximize defence against phishing and other human centred attacks.
77% of all data breaches involve stolen or compromised credentials4
-
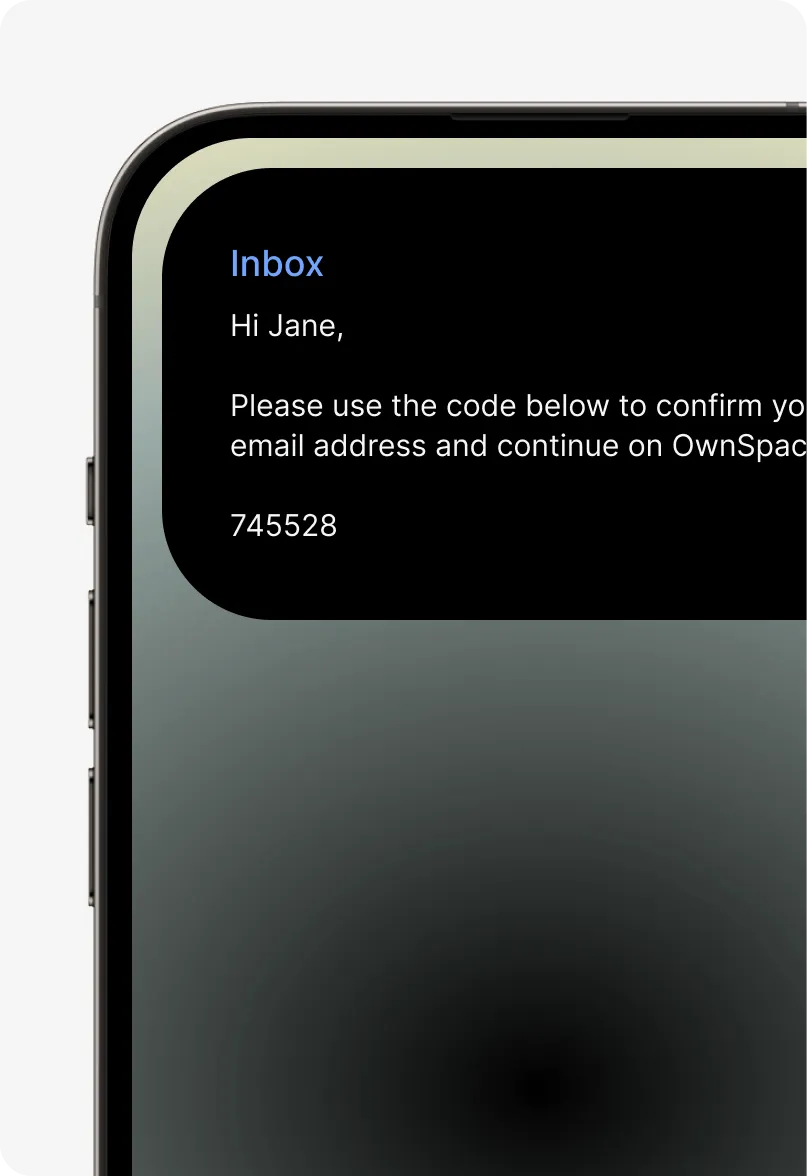
Magic codes – not passwords Passwordless auth
Nobody likes passwords – and they’re a high security risk. Give your customers a secure way to sign in to your apps and websites using just an email address. A seamless, secure experience — combining the benefits of multi-factor authentication with the security of email.
-
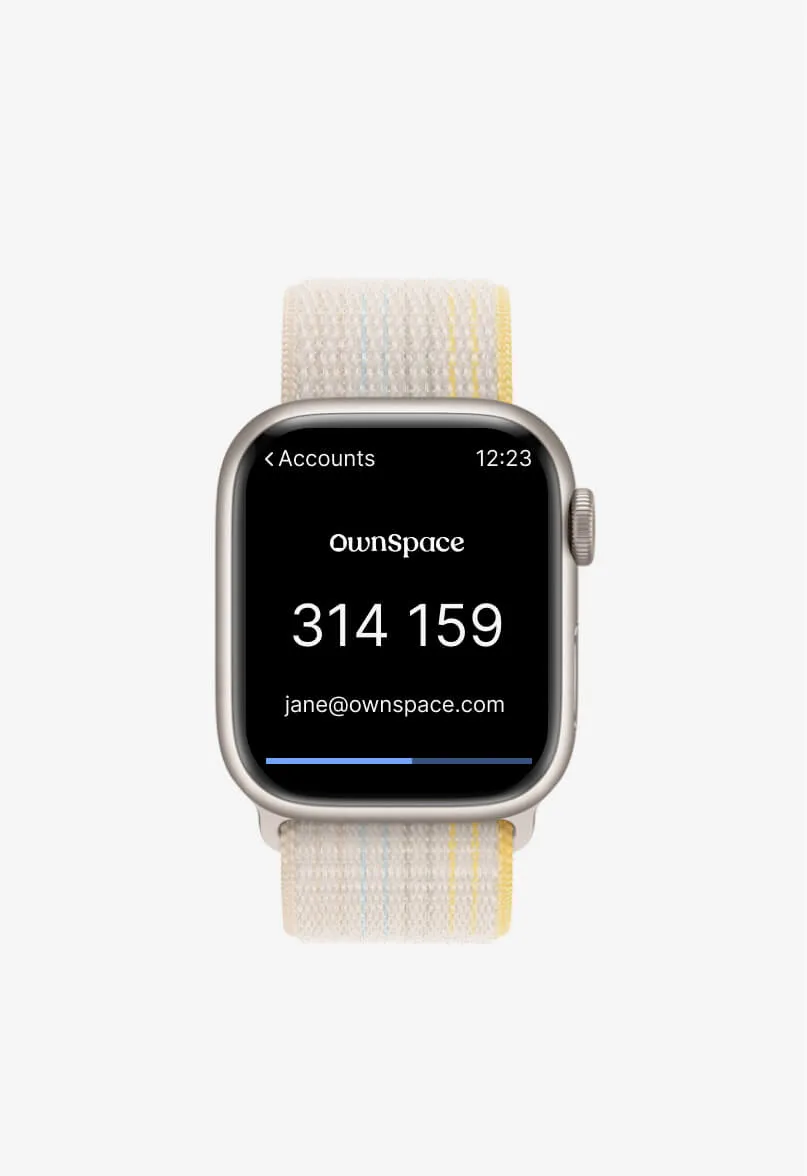
Authenticate with any authenticator app – anywhere Multi-factor authentication
Give your users access to advanced authentication options, protecting them from reused or breached passwords.
Add an extra layer of protection with identity verification through a second device, sms, or time-based one-time passcodes. Quickly and easily integrate with any authenticator app.
Google authenticator
Authy
1password
-
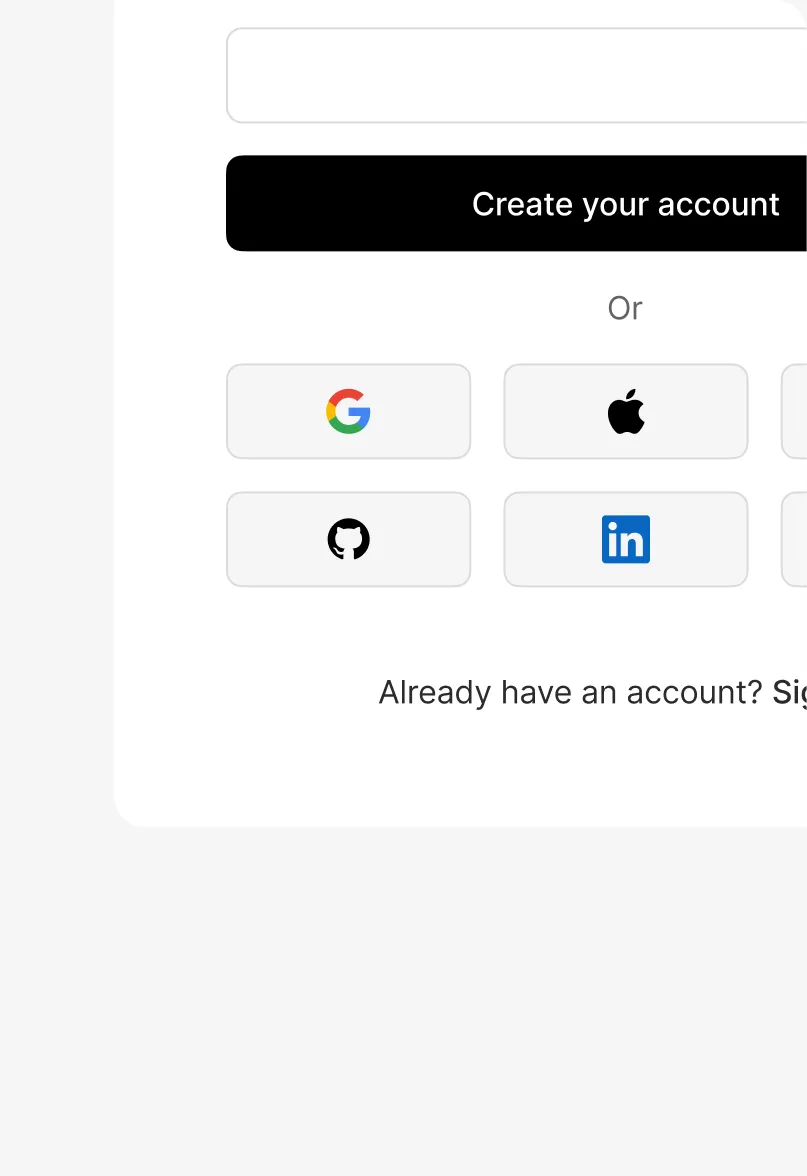
Add social auth options in seconds Social auth
Your users already know and love social login because they use it every day. Toggle on the SSO options they want and massively increase security, trust, conversion and data-quality with one click.